Консультация ветеринарного врача играет ключевую роль в обеспечении здоровья и благополучия домашних животных.
В мире цифрового маркетинга TikTok занимает особое место благодаря своей динамике и широкому охвату
Мясо играет важнейшую роль в питании собак, так как является источником высококачественного белка, необходимого
Мини мальтезе – это уменьшенная версия известной породы мальтезе, отличающаяся своими компактными размерами и
Этикет подачи цветов также важен, как и их выбор. Вручая букет, следует делать это
Усыпление собаки – это ответственный и сложный процесс, который должен проводиться только квалифицированным ветеринаром.
Вельш-корги - это порода собак, завоевавшая сердца многих благодаря своему уникальному внешнему виду и
Ветеринарные аптеки обеспечивают доступ к качественным лекарственным средствам, что особенно важно для владельцев, стремящихся
Красная книга России является официальным документом, который содержит информацию о редких и находящихся под
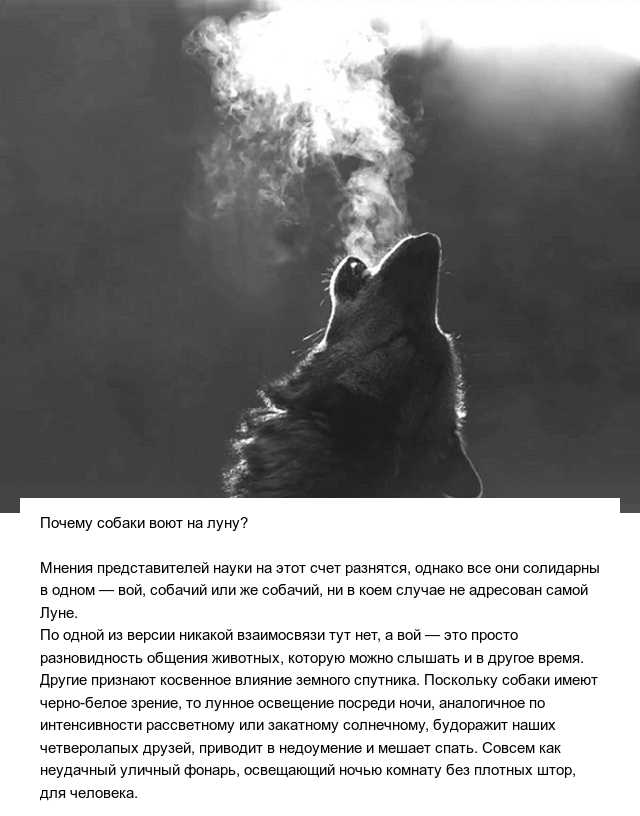
Собака воет целый день: почему она это делает и как реагировать на это? Особенности
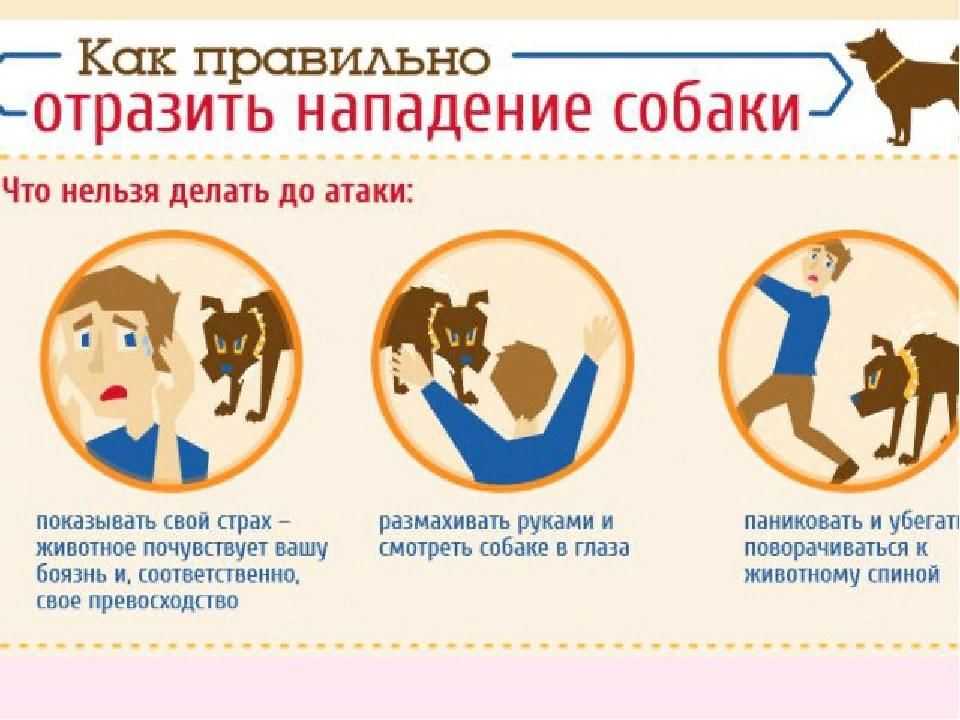
Собака кусается потому, что для нее это естественно. Главная проблема состоит не в том,
Существует несколько способов как можно предотвратить или исправить прыжки собаки на людей. Если у
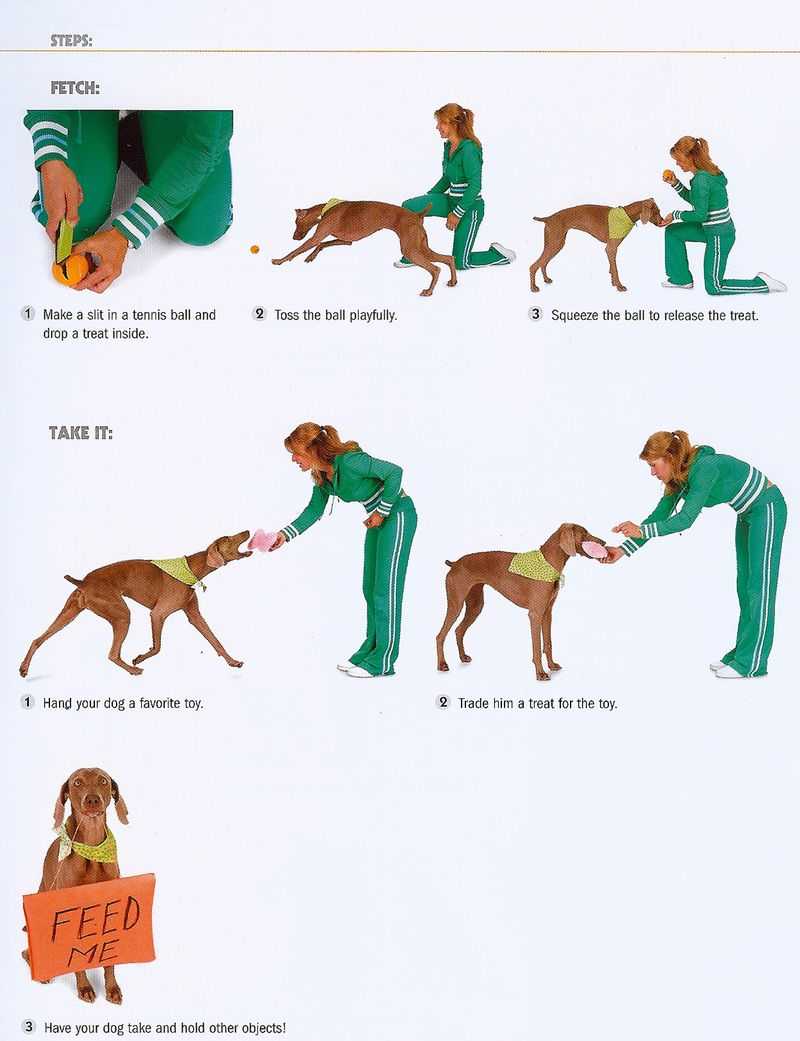
Методы и правила дрессировки. Инструкция и видео уроки. Как выпонять команду правильно. Закрепление изученного.
Многие люди уверены, что собаки кусаются, потому что "они для этого созданы". Но собака
Статья расскажет о том, как приучить щенка к туалету на улице с первых дней
Все, что необходимо знать о том, как приучить собаку к будке во дворе быстро
О том, как самостоятельно обучить собаку простым командам. С чего начать занятия и на
Как научить собаку команде "фас", не навредив психике животного. Методы обучения питомца, на что
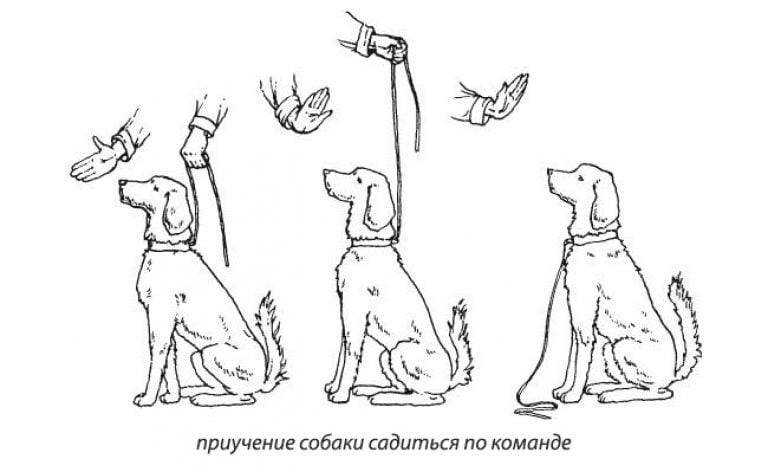
✅ 10.10.2019 Как приучить собаку оставаться на месте Как научить собаку команде Место «Место»
Полезные рекомендации специалистов о том как научить собаку командам «нельзя» и «фу» самостоятельно, но
Предлагаем вам научить собаку команде «Фу», используя нашу пошаговую инструкцию и советы от профессионального
Притворяться мертвой - отличный собачий трюк, который развлечёт ваших гостей и друзей. .
Давно хотите научить собаку приносить палку или игрушку, но не знаете как? В этом
Команда «Голос» является частью обязательных команд для собаки. Она входит в базовый норматив любого
Как отучить собаку лазить на стол. Причины некорректного поведения. Способы избавления от воровства и
✅ 05.11.2019 Как отучить собаку лаять на других собак Без лишнего шума — как
В 2021 году по данным Mars Petcare в российских семьях жили 63,5 млн собак